
ProSymbols/The Noun Project/Andrew McGill
We Built a Fake Web Toaster, and It Was Hacked in an Hour
It's really, really easy for hackers to find unsecured devices.
Last week, a massive chain of hacked computers simultaneously dropped what they were doing and blasted terabytes of junk data to a set of key servers, temporarily shutting down access to popular sites in the eastern U.S. and beyond. Unlike previous attacks, many of these compromised computers weren’t sitting on someone’s desk, or tucked away in a laptop case—they were instead the cheap processors soldered into web-connected devices, from security cameras to video recorders. A DVR could have helped bring down Twitter.
Great, I thought as I read the coverage last week. My DVR helped bring down Twitter. (Probably not, at least this time—the targeted products were older than what you’d find in most American homes, and less protected.) But the internet is huge! There are around a couple billion public IPv4 addresses out there; any one of those might have a server, a desktop computer, or a toaster plugged in at the other end. Even if the manufacturer of my gadget gave it a dumb and easily guessed password, wouldn’t it be safe in this sea of anonymity? How would the hackers find me?
I don’t actually own a wireless toaster. But I devised a test. Renting a small server from Amazon, I gussied it up to look like an unsecured web device, opening a web port that hackers commonly use to remotely control computers. Instead of allowing real access, though, I set up a false front: Hackers would think they were logging into a server, but I’d really just record their keystrokes and IP addresses. In cybersecurity circles, this is called putting out a honeypot—an irresistible target that attracts and ultimately entraps hackers and the scripts they use to find vulnerable servers.
Here’s what my particular honeypot looked like, if you tried to log in:
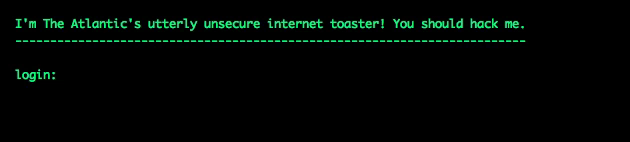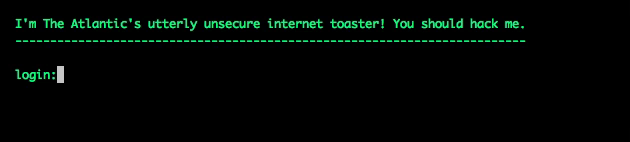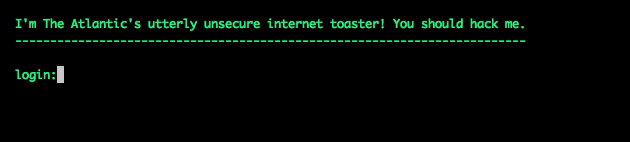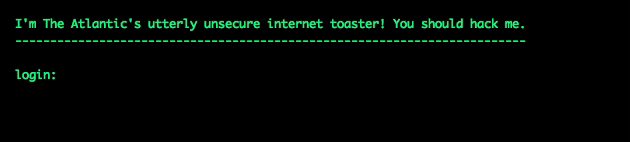
I switched on the server at 1:12 p.m. Wednesday, fully expecting to wait days—or weeks—to see a hack attempt.
Wrong! The first one came at 1:53 p.m.
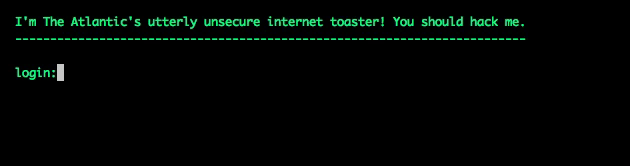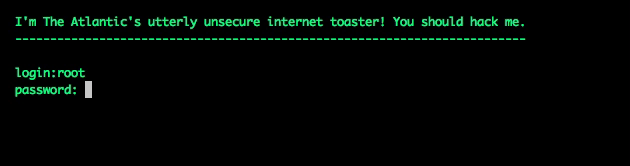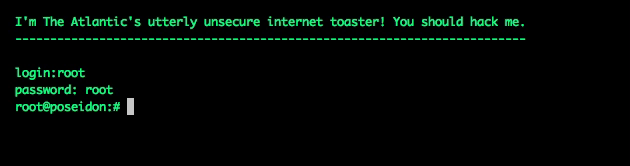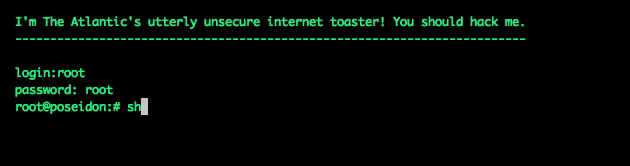
This graphic is a simulation—a bot’s-eye view, if you will—but it’s the actual sequence of commands the hacking script used. It tried a common default username and password (root/root) and executed the “sh” command, giving it the ability to run programs and install its own code. My fake toaster doesn’t allow that, of course—it just cuts the connection.
The next hacking attempt, from a different IP address and using different login credentials, came at 2:07 p.m. Another came at 2:10. And then 2:40. And 2:48. In all, more than 300 different IP addresses attempted to hack my honeypot by 11:59 p.m. Many of them used the password “xc3511,” which was the factory default for many of the old webcams hijacked in last week’s attack.
The last attempted hack came 26 minutes ago using the username "root" and the password "xc3511." (Yes, those are live figures; they were updated when you loaded this page.)
I’ll admit this volume of attacks might not be typical. I hosted my fake toaster on a virtual Amazon server, not an actual toaster hooked up to residential internet. Hackers aren’t typing these passwords themselves—they’ve programmed bots to do the hard work for them, scanning through thousands of open ports an hour. And I’d bet those scripts are trawling Amazon’s range of IP addresses more frequently in hopes of hacking vulnerable rookies. (If that has happened to me without my knowledge, I am very sorry and please don’t hurt me.) But my experience matches what security firms have seen. It is now within the capability of hackers to literally scan the entire internet, looking for vulnerable servers with open ports. And every hacked computer adds another recruit to the search effort, shortening the time required geometrically.
Matthew Prince, the cofounder and CEO of Cloudflare, said anyone hooking up a poorly secured IP device to the internet can expect to see that gizmo hacked within a week, if not much sooner.
“Assuming it’s publicly accessible, the chance [of being hacked] is probably 100 percent,” he said. “The IPv4 address space just isn’t that big. You can now run a scan across that entire space in hours, especially if you have a big botnet. The scans for vulnerability are continuous, and if anything, have accelerated over the last couple of years.”
This doesn’t mean that every Internet-of-Things device is vulnerable. Most things that you connect to the web through your home WiFi are probably okay: Your router kills most incoming hacking attempts. (Of course, if your router is compromised...) You have more to worry about if your device hooks up to your modem directly, which is more common in industrial settings.
All the same, the vastness of the internet can no longer protect us. I can’t count the number of sloppy things I’ve done, security-wise, because I thought I was small enough to escape notice—reused passwords, put private keys in code, left servers open to the world. Nowadays, even the most obscure among us can be found by a roving script, and in a startlingly small amount of time.




